Cryptocurrency payments are becoming more and more common in everyday life. They are being used to pay for goods and services, as well as for many other purposes. And since digital assets are popular, cryptocurrency wallets are increasingly affected by hackers who want to steal other people's funds.
If there are means of hacking — there must be means of protection. Therefore, every owner of digital assets is interested in protecting themselves from hackers as much as possible. Especially since today there are already proven, reliable ways, which will be described below.
How Does a Cryptocurrency Wallet Work?
A cryptocurrency wallet is a repository of public and private keys, with the help of which the owner gets access to their digital assets. Cryptocurrency wallets can be classified in several ways:
- by management — centralized (managed by the bank), decentralized (managed by the user);
- by place of key storage — custodial (the key is held by the bank) and non-custodial (the user keeps the key), hot and cold crypto wallets (presence or absence of a permanent connection to the network);
- by storage location — desktop (on a hard disk), mobile (on a smartphone), online (stored remotely on a server).
Cryptocurrency is safe as long as the public and private keys of the wallet are known exclusively to its owner. These keys look like long chains of symbols — numbers and letters and are used for encryption during transactions. Compared to conventional means of payment, the public key is a bank card number, phone number or account login; the private key is a pin code or password, without which authorization is impossible.

If an intruder gets access to the keys, it can be considered that the wallet is already empty. Since it is not issued by a bank, it has no insurance system, so the user needs to take care of security themselves.
Of course, today's cryptocurrency wallets are no longer as vulnerable as they were in the era of the emergence of cryptocurrency, but hackers are not slumbering either, coming up with new ways of hacking.
If you are now in the process of choosing the right cryptocurrency wallet for you, we advise you to read our article: «Trust Wallet Review: Advantages & Features».
Cryptocurrency Wallet Hacking Tactics
To reliably protect from theft, you should learn more about how attackers operate before you start a cryptocurrency wallet.
Phishing
The most common way to steal someone's money is to lure a person to a phishing website. Such a website can look very similar to the official one, for example, copying a cryptocurrency exchange, where the user often goes. Without paying attention to the difference of the address in the line (especially if the difference is insignificant), the user enters the data for authorization.

Of course, after that, the victim does not get access to the account. But the fraudsters who created the phishing website steal the authorization data — that's why it's so important not to click on suspicious links.
Remember that links to phishing websites are usually distributed through social networks and messengers on behalf of official accounts.
Ransomware (Trojans)
Once launched, such a program scans folders for data related to cryptocurrency wallets. Trojans can also encrypt information and lock the device with a ransom demand for the attacker. Modern versions of ransomware may not manifest themselves but take some of the device's power for mining.
For the virus to start working, the user must launch the trojan themselves, so they are often disguised as useful applications, games, video files, and so on. It is worth installing a good antivirus to avoid losing your financial assets and personal data. You should also have a separate backup of valuable information — and, of course, do not open suspicious e-mail attachments.
Keyloggers
This is the name given to applications whose only function is to memorize the sequence of keystrokes made by the user. Keyloggers are most often distributed with other products, which is why it is so important to download products only from trusted sources.
Public Wi-Fi networks
When using a wireless internet connection whose security cannot be verified, users put their sensitive data at great risk. Modern hackers can easily steal information by simultaneously connecting to the same Wi-Fi network.

SMS interception, SIM card duplication
Initially, confirmation by sms-code or call looked like a way to protect yourself from hacking. However, now attackers can intercept sms, duplicate sim card and get access to information. To avoid this, it is wise to use other security methods rather than using your own sim card for authorization. It is also recommended to securely protect access to your mobile operator's personal account.
Hacking mobile crypto wallets
As practice shows, owners of Android phones more often become victims than those who use iPhones, although the latter are not completely protected from counterfeiting. Attackers create and upload to the store an application that imitates the official wallet by design and name, and when it is launched, they gain access to the data.
Browser extensions and plugins
By downloading unverified extensions, owners can easily get a malicious application from hackers instead of a useful tool. As in other cases, it will not provide access to the wallet, but will steal the user's data and transfer it to the attackers.
How to protect a cryptocurrency wallet from hacking?
Knowing how to properly protect your assets from intruders, you can reduce the risks of hacking to almost zero. There are several options for protection.
Do not keep all your money in one wallet
This option assumes that even if some of the funds are stolen, the owner will not lose them entirely — however, in fact, this is not really a method of protection, but rather — risk diversification. The user simply recognizes that they cannot be sure of the safety of their assets, and tries to reduce losses in advance. We recommend reading the article: «Locking Down Your Crypto: Tips for Secure Funds Storage».

Separate device
If you store cryptocurrency on a separate computer or, for example, on a USB flash drive without a network connection, then most of the time such a hardware cryptocurrency wallet will be inaccessible to attackers. Although at some point the user will still make transactions — and it is then that he will be at risk. It will also be necessary to completely limit the device, that is, do not use the computer for web surfing, and the drive — for storing other data.
Backup
Since nothings can protect funds for one hundred percent, the user can also create multiple copies of the cryptocurrency wallet and store them separately from each other. The available copies should be updated periodically.
Complex password
Many users are in the habit of using the same password for different purposes. In such a case, it is easy for hackers to gain access to a cryptocurrency wallet by hacking into an e-mail account or an online game.
You can avoid this by using a separate password for it. This password should be a random set of ten or more characters: letters, numbers, punctuation marks, then it will be almost impossible to guess it. Dispatcher programs help to organize passwords and update them without keeping everything in your head.
Also, any modern cryptocurrency wallet like Binance or another similar one usually uses seed phrase to generate private keys.
Two-factor authentication
This method is more reliable than confirmation via sms or e-mail, since protection from unauthorized access is provided from the beginning. The generated code does not need to be forwarded, which reduces the risk of hacking.
The Google Authenticator application is often used for this purpose. After connecting two-factor authentication, you will be provided with backup keys. These can come in handy in case you don't have access to a device with the app installed.
Multi-signature
The method works similarly to confirming a document with several signatures or visas. Multi-signature implies that the transaction must be confirmed from several different accounts.

Secure device storage
When using a separate device for your cryptocurrency wallet and its backup, it is wise to store it at home. The best protection will be provided by a vault — home or bank one. Key-value devices are not recommended to be carried around unless absolutely necessary.
Do not leave wallet details on your website
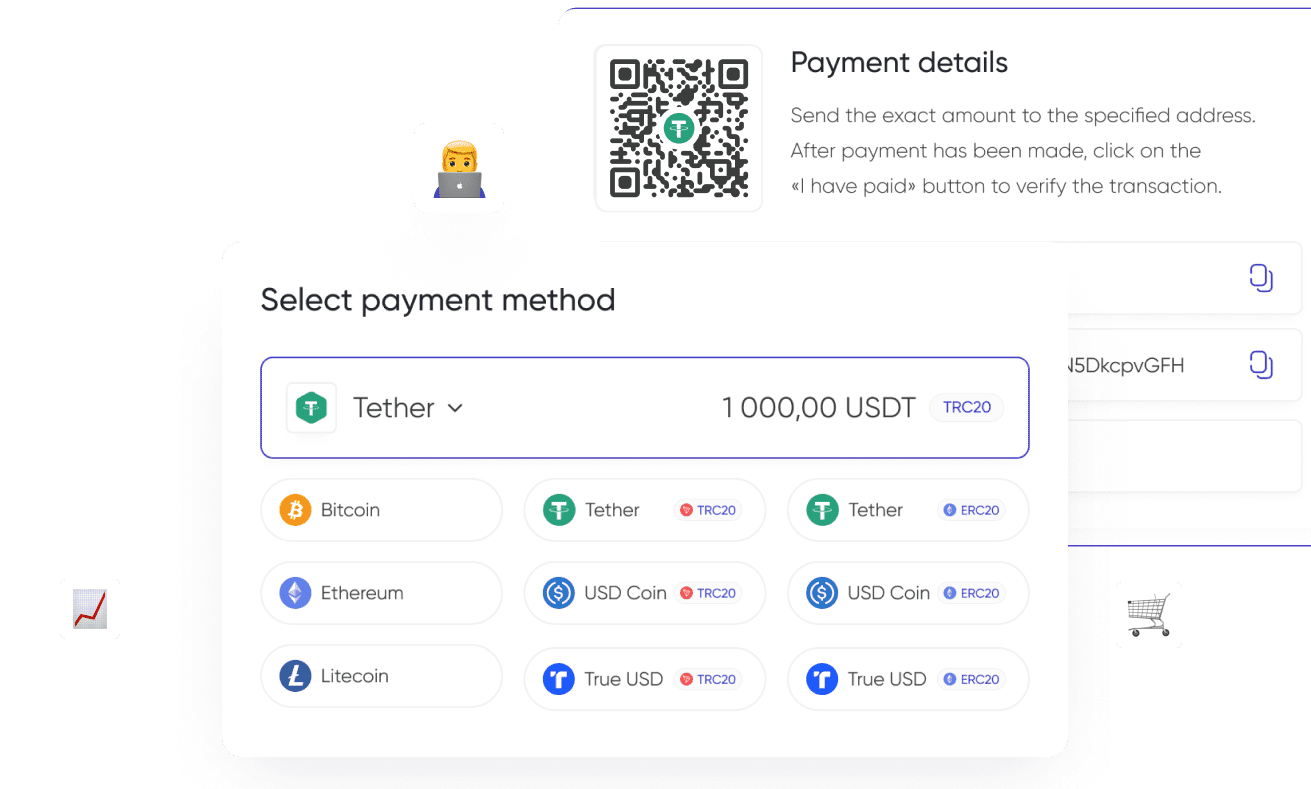
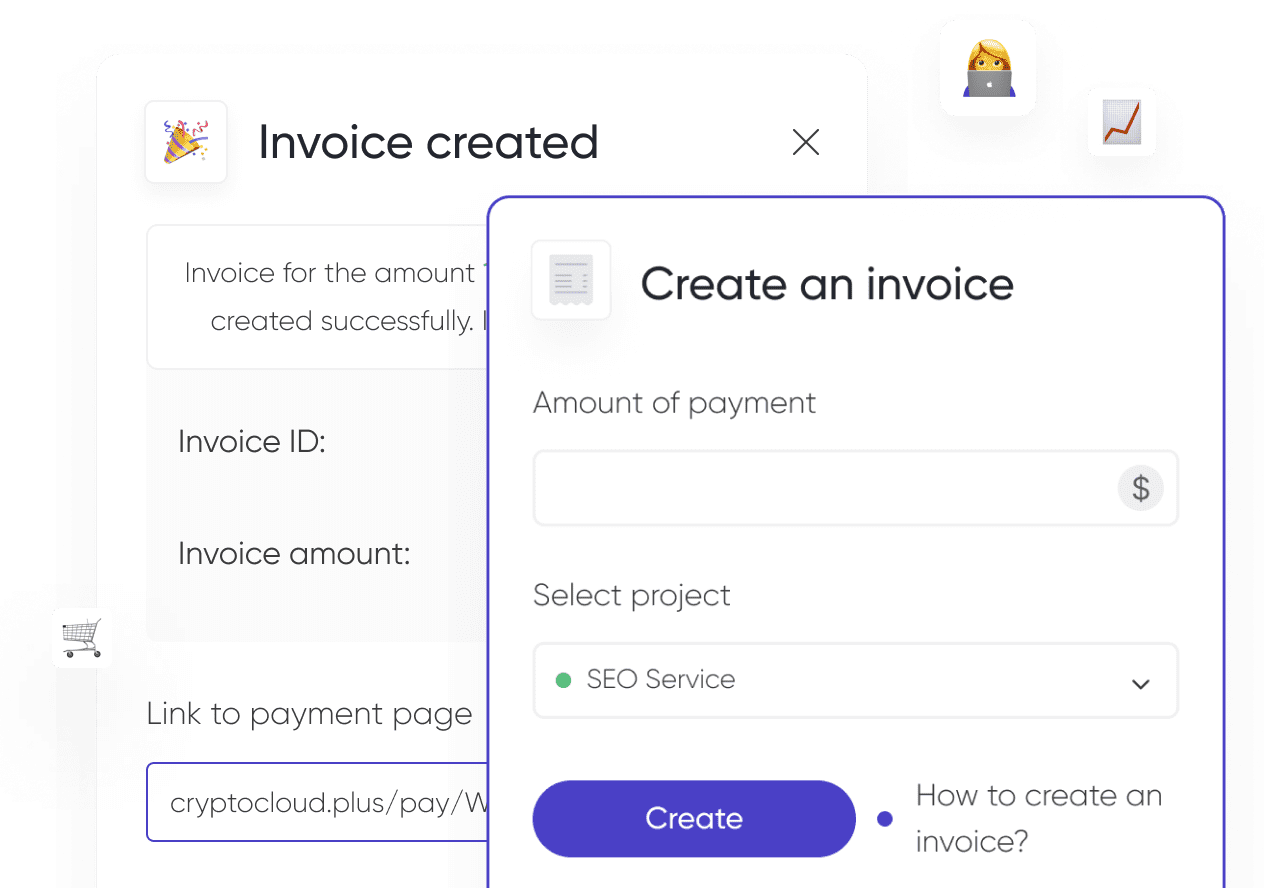
Often business owners leave the cryptocurrency wallet address on the website to accept payments, but this greatly increases the level of risk. Avoid this by connecting a reliable and convenient crypto processing service such as Cryptocloud. This is a service specifically designed to process payments quickly and securely.
In addition, you can use a special protocol, WalletConnect, to establish a secure connection to the wallet. More details about the service were given in the article.
What Should You Do If Your Cryptocurrency Wallet Has Been Hacked?
If there is a possibility that your wallet has been hacked or that it has been accessed by third parties, there are several steps that need to be taken immediately:
- If access to the cryptocurrency wallet is not lost — transfer accumulated assets to another wallet or convert to fiat currency.
- Start working from a new device. Already through it, change passwords, including mail and other services passwords.
- If there is such a function, log out of the wallet from all the devices where you had access.

- Text to the technical support of the online wallet. Attach all data on transactions made by hackers.
- Completely reset the settings of the smartphone or computer that was accessed. Do not use the device for access anymore: some Trojan programs are saved on formatted media as well.
The actions listed above will increase the likelihood of keeping your accumulated assets at least partially intact. If the funds were transferred from your wallet, due to the specifics of blockchain technology, it will not be possible to return them.
How to Accept Cryptocurrency Payments?
Taking care of the security of a cryptocurrency wallet is a task that the owner settles on their own. Attackers come up with more and more new ways of hacking, keeping up with progress. One of the most effective ways for entrepreneurs to protect their digital assets is to connect crypto processing to process payments made, rather than leaving wallet data on the website.
Our CryptoCloud service offers maximum opportunities for cryptocurrency transactions. You don't have to disclose your personal wallet data to anyone — the integrity and security of cryptocurrency is greatly increased due to this.